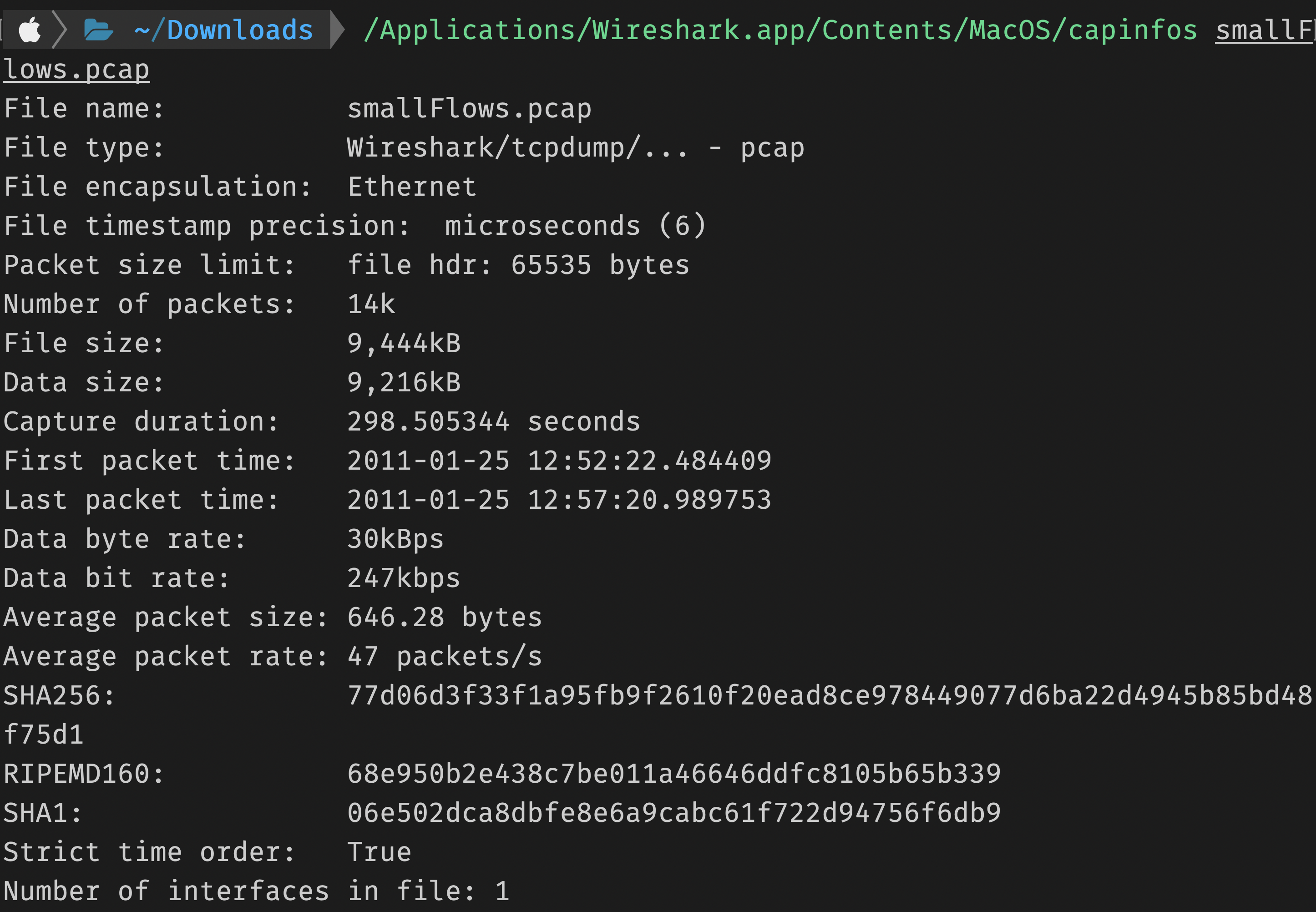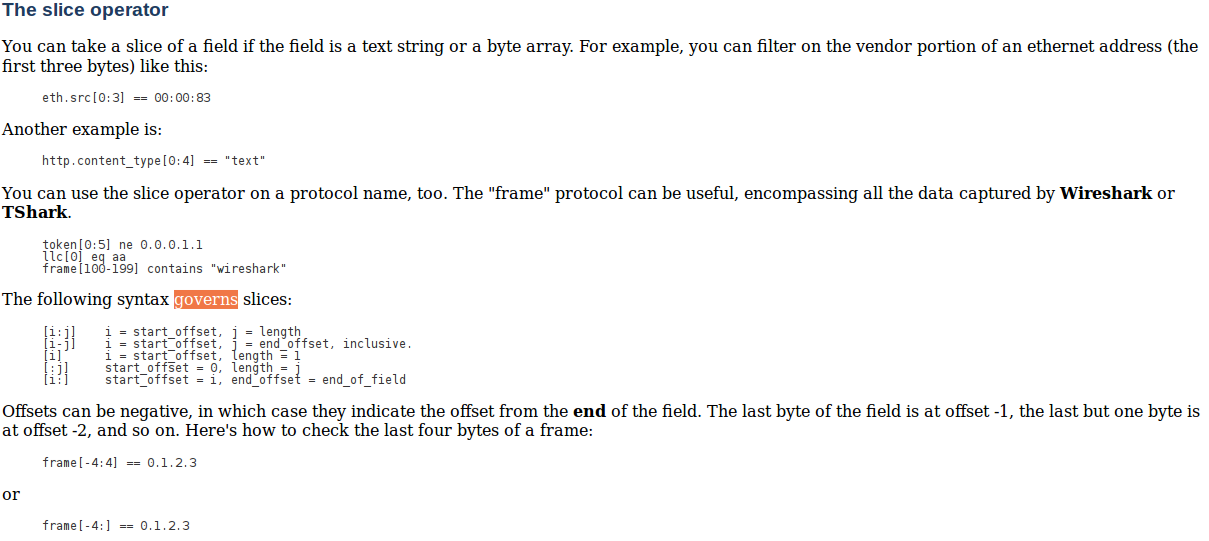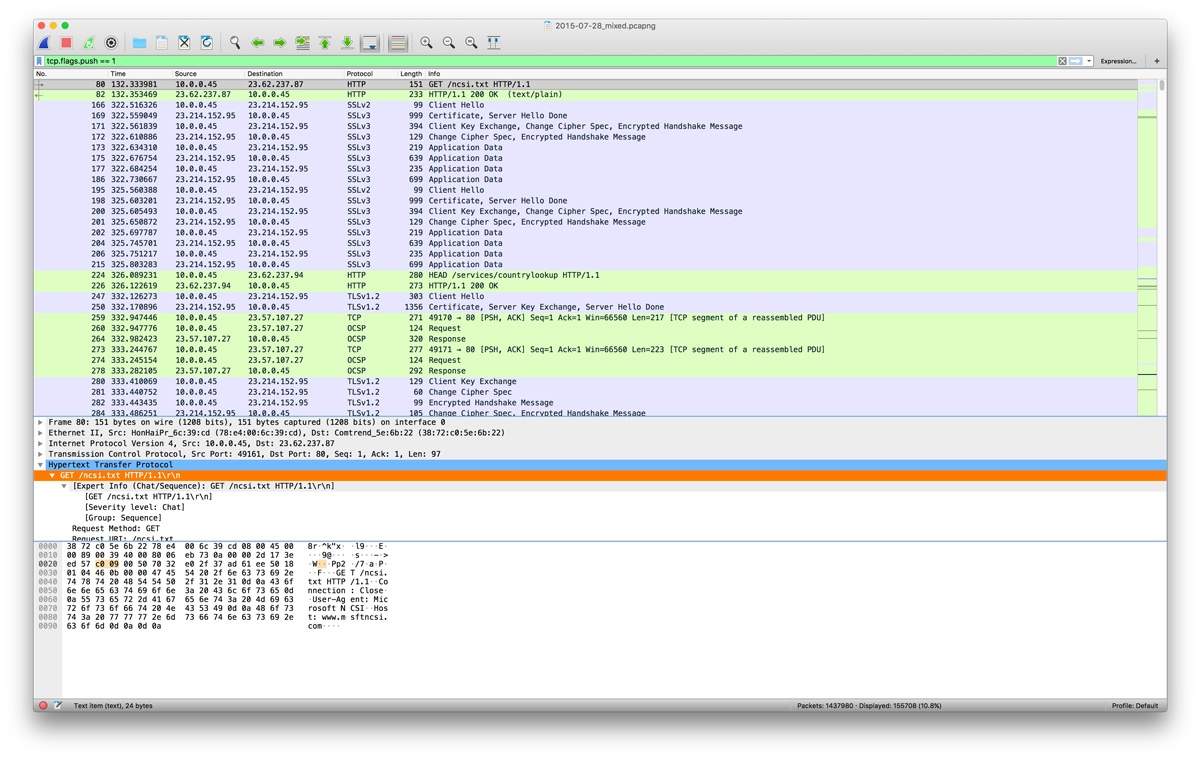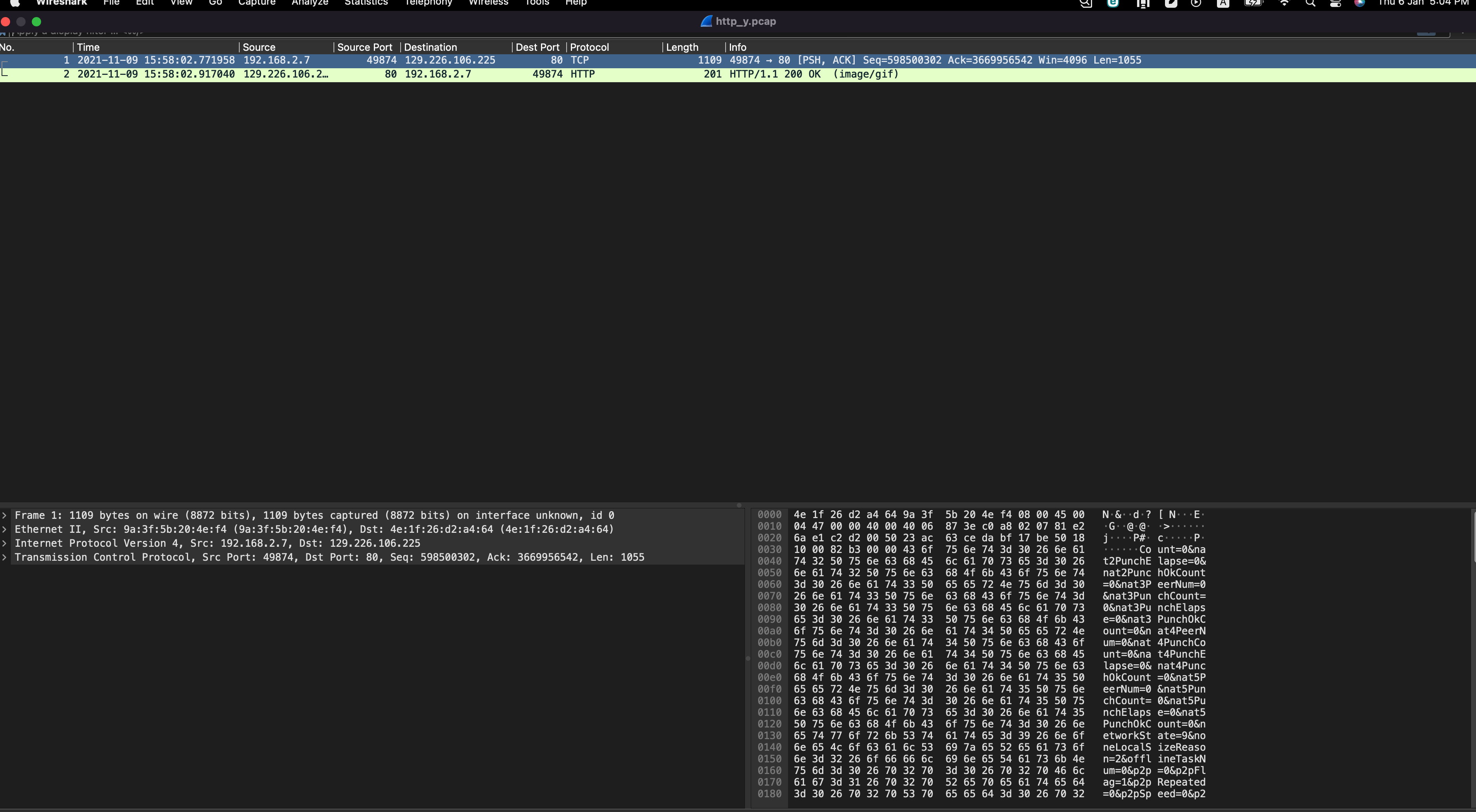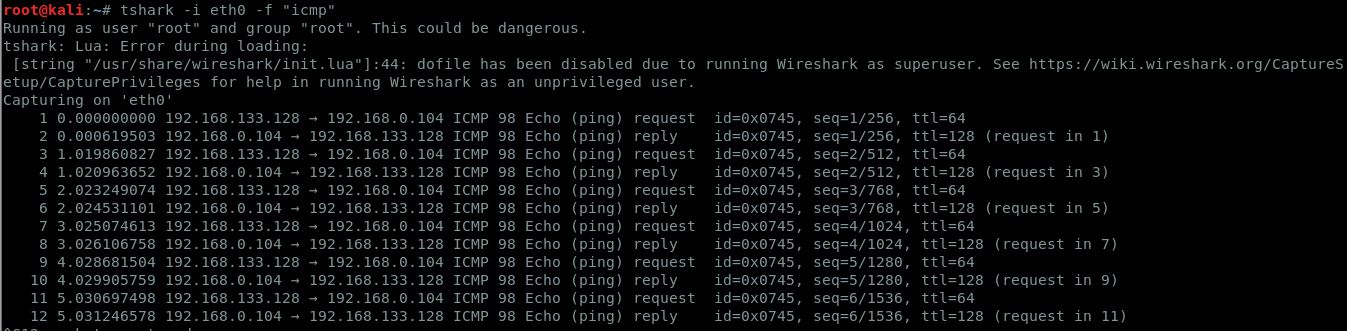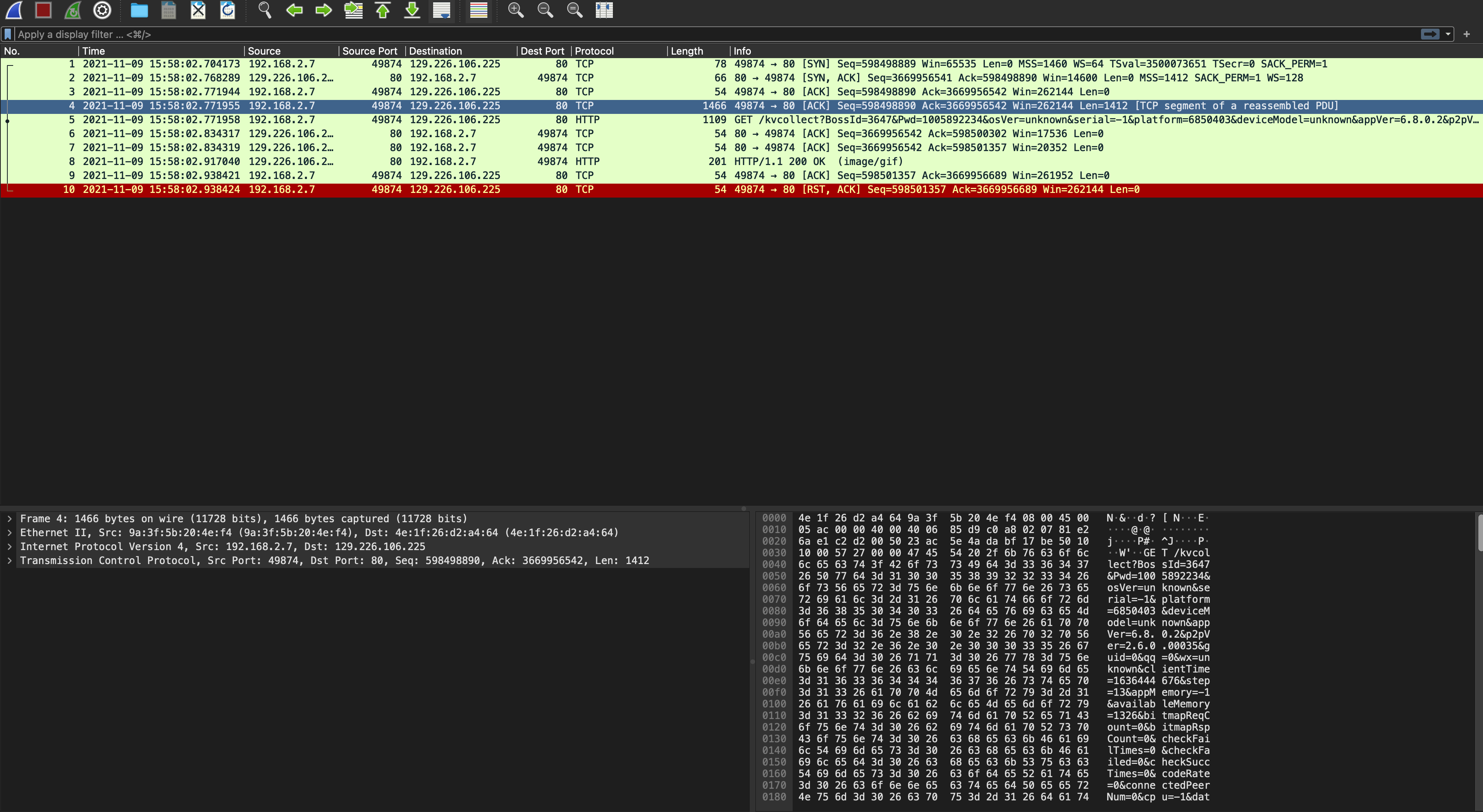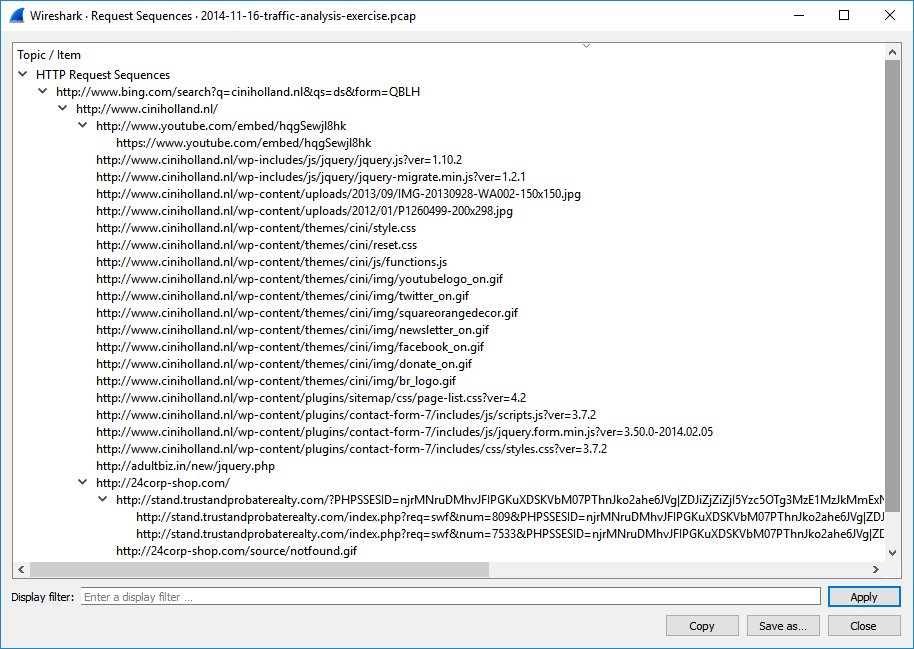
SANS Internet Storm Center SANS Internet Storm Center - A global cooperative cyber threat / internet security monitor and alert system. Featuring daily handler diaries with summarizing and analyzing new threats to

So Who Needs a GUI in Cybersecurity? | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

Introduction to TShark. Hello guys I am Sudeepa Shiranthaka and… | by Sudeepa Shiranthaka | InfoSec Write-ups